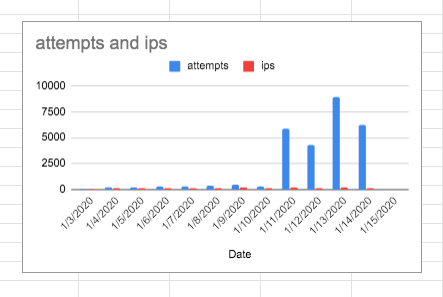
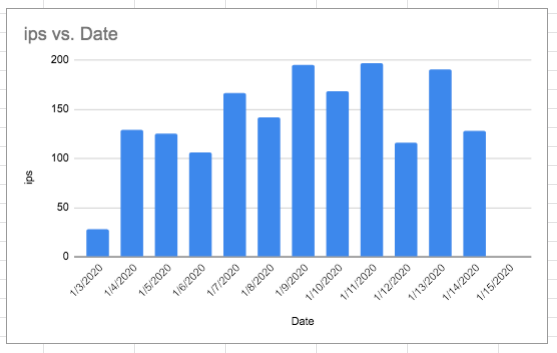
Hi I’m very proud to announce that my application (which I still haven’t found a name for!) is ready for beta release. It’s a very light command line app that uses log data for security hardening, so if you use Ubuntu, debian or linux (and or nginx or apache2) and are comfortable with the command line then please do get in touch. At this stage it’s a fairly simple app and in effect a security tool for those of us who can not afford thousands of dollars towards their own IDS.
This application will probably be most useful for smb running their own sites (small aws installs for example) for people who want extra security, and to stop a lot of the “noise” that hits the average web server.
If you want more information, have a look at the intro vid I made that is put up on youtube..
All I ask is that you supply the version of ubuntu / linux that you’re using and that after looking at the app take the time to fill in a short survey.
Look forward to hearing from you
Regards Steve Abrahall
PS if your interested email me at
steveabrahall AT gmail DOT comm
To find out what version of the os your usinglsb_release -a