So as a few of you know I’m this crusty old Sys Admin dude. I have a number of machines that I look after, and they are nearly all Linux machines. They are on pretty much twenty four seven, this site is an example of such an endeavor.
So as a few of you know I’m this crusty old Sys Admin dude. I have a number of machines that I look after, and they are nearly all Linux machines. They are on pretty much twenty four seven, this site is an example of such an endeavor.
But the internet has a problem – it’s the continual attack on any machine (Mac, Windows Linux, Unix or something else) and any service that said machine might be running.
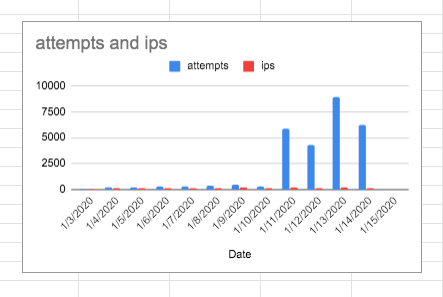
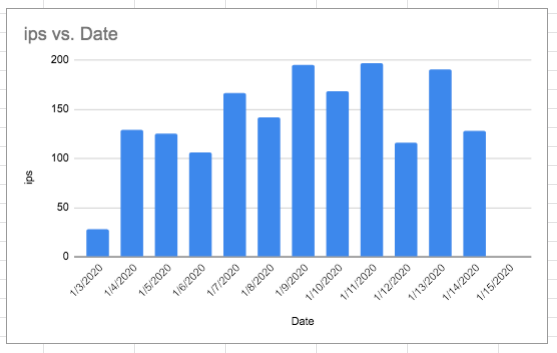
It’s not uncommon for someone to attempt to attack this machine every day. Probably the worst I’ve seen is about 30 thousand attempts in one day. Typically it’s about 1- 3 K, and I have been whittling this number down … there is a way to manage this.
1 Record what the offensive ip address are (auth log is your friend in this instance)
2 Add these offensive address to the firewall “or better” so that they will not ever have any access, even if it to just rattle the locks on the doors of your computers.
Typically the command, to block an ip address is something like this, it’s not a complex thing .
sudo iptables -A INPUT -s 10.1.1.1/32 -j DROP
People are concerned that one may block out legitimate traffic (and admittedly this is important, especially if you do accidentally add your own ip address!…. do you have physical access to the machine? a plan B?). But don’t let me scare you, what I’m talking about is not complex (just take care!).
When you think about it there are 4,294,967,296 usable version 4 ip address. My current block list on this small machine is about 880 of these…. that is about 0.0000204891% of all available ip v4 address. It’s not much and my machine is rather low tech.
But the problem is routers. My own network is based on a router that is controlled by my isp. I don’t really have total control over this machine, but it would be good if I could manage that process a bit. But the isp says no – you can have 3 settings!
The up shot is, if I’m serious about security and running may own server from home … I have to manage the abuse from a machine level or add an additional router! ?
It would be better to manage it from a router level because then every machine behind that router / firewall would be protected. But we haven’t really made this jump. I also understand that segmenting the internet is not a good thing but I’m happy with my 0.0000204891 % reduction. I don’t feel bad about this.