A while back I wrote sshfail. It’s a script to look at attempts on the ssh protocol on servers. You can find it up on git hub if your interested and want to install in your self. https://github.com/nevetsanderson/sshfail .
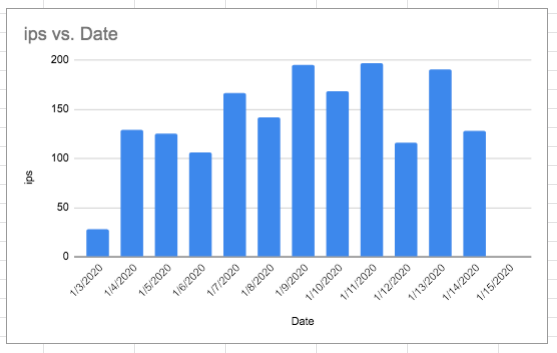
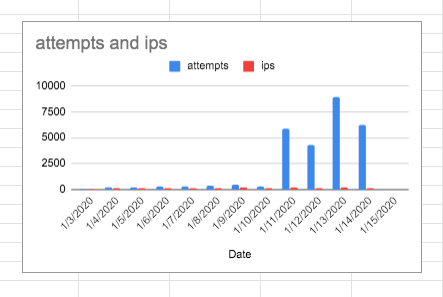
The interesting thing is that even if you use a non standard port to run ssh on (which is what this data relates to) it’s only a matter of time before modern hackers or bots or some Bs8dutard’s find that information and it gets propergated. Have a look at this raw data.
| Date | Attempts | ips |
| 1/3/2020 | 28 | 28 |
| 1/4/2020 | 239 | 129 |
| 1/5/2020 | 204 | 125 |
| 1/6/2020 | 337 | 106 |
| 1/7/2020 | 322 | 167 |
| 1/8/2020 | 386 | 142 |
| 1/9/2020 | 452 | 195 |
| 1/10/2020 | 273 | 169 |
| 1/11/2020 | 5873 | 197 |
| 1/12/2020 | 4346 | 116 |
| 1/13/2020 | 8892 | 191 |
| 1/14/2020 | 6192 | 128 |
| 1/15/2020 | 0 | 0 |
As you can see things got ugly after about 11 days… from 28 to 5873 attempts on the server per day and within 2 weeks. Also worth considering is how did things go from weeks of no one being able to detect this, to 28 ip address suddenly finding my machine on the same day and then it increasing to 195 (Jan 3-9). I’d love to know what’s going on in the background. How is information is being propergated?
So as you can also observe on the 15 th, I changed the port and things have been have quiet since then but the issue is… If I hadn’t been observant and actually looked at the numbers then I’d be giving the bad guys a chance at reeking havok…
Stay safe out there people, and actually look at your log data!